 Apache Geode
CHANGELOG
Apache Geode
CHANGELOG
How Gemcached Works
Applications use memcached clients to access data stored in embedded Gemcached servers.
Applications can use memcached clients that are written in Python, C#, Ruby, PHP, and other programming languages. Each memcached server in a cluster stores data as key/value pairs. A memcached client maintains a list of these servers, determines which server has the required data, and accesses the data directly on that server.
To integrate memcached with Apache Geode, you embed a Gemcached server within a Geode cache server. These Gemcached servers take the place of memcached servers. The memcached client uses its normal wire protocol to communicate with the Gemcached servers, which appear to the client as memcached servers. No code changes in the clients are needed. Geode manages the distribution and access to data among the embedded Gemcached servers.
As shown in Gemcached Architecture, memcached clients, which ordinarily maintain a list of memcached servers, now maintain a list of embedded Gemcached servers. If more embedded Gemcached servers are added to the cluster, the new servers automatically become part of the cluster. The memcached clients can continue to communicate with the servers on the list, without having to update their list of servers.
Figure: Gemcached Architecture
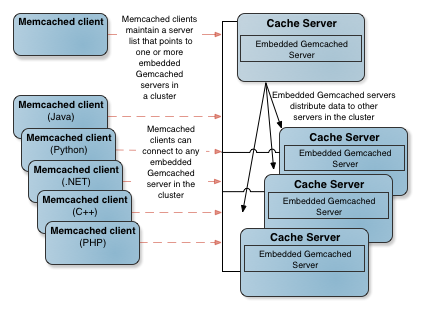
Memcached clients use the memcached API to read and write data that is stored in memcached servers; therefore, client-side Geode features are not available to these clients. Gemcached servers, however, can use Geode’s server-side features and API. These features include the following. (For more detail, see Advantages of Gemcached over Memcached.)
- Data consistency and scalability.
- High availability.
- Read-through, write through, and write behind to a database, implemented from within the distributed Geode cache.
- Storage keys and values of any type and size.
- For applications, a choice among partitioned and replicated region configurations.
- Automatic overflow of data to disk in low-memory scenarios.
- Efficient persistence of data to disk.
- Configurable expiration of cached data.
- Configurable eviction of cached data.